Using Flow Data to Optimize Firewall Rules: Best Practices and Cloud Migration Insights
By: Eric Graham
July 22, 2025
As enterprise networks evolve and shift toward hybrid and cloud-native architectures, security teams are under increased pressure to manage firewall rule sets that are effective and efficient. One of the most consistent sources of data in this process is flow, network telemetry collected from routers, switches, firewalls, and cloud gateways.
Flow data, such as NetFlow, IPFIX, and sFlow, provides a granular view of network communications—identifying who is talking to whom, over what ports, using which protocols, whether bidirectional communication is established, and for how long. When harnessed strategically, this data becomes a powerful asset for:
Auditing existing firewall rules
Identifying redundant or obsolete allow lists
Tracking application dependencies
Understanding if applications are successfully communicating bidirectionally
Safely tightening security postures during cloud migrations
Below, we explore how and why you should use flow data to tune your firewall policy lifecycle.
Why Firewalls Need Continuous Optimization
Traditional firewall rules are often static. They accumulate over time, forming bloated rule sets filled with unused or legacy entries. These outdated rules:
Introduce security blind spots
Increase operational complexity
Slow down firewall performance
Risk of unintentional overexposure of services
Make troubleshooting allow and block rules difficult
During cloud migrations, this challenge intensifies. You might be lifting applications from data centers to VPCs or re-platforming to microservices. In either case, you need to determine:
Which services still depend on the existing firewall rules?
Are clients still using specific ports/IPs?
What application traffic can be safely rerouted, blocked, or deprecated?
This is where flow data shines.
Best Practices for Using Flow Data to Drive Firewall Rule Decisions
1. Map Application Dependencies Before Rule Changes
Use Case: You plan to migrate an internal HR app to the cloud.
Action: Analyze historical flow records (30–90 days) for the app’s IP and port range to determine all client IPs, dependent services, and ports in use. Flow data can reveal hidden dependencies (e.g., LDAP, NTP, internal APIs) that would otherwise break post-migration.
Tip: Visualize the app’s communication graph using a flow analytics platform to see real-time and historical connectivity patterns.
2. Validate the Necessity of Existing Allow Rules
Use Case: You want to clean up old firewall rules that “no one dares touch.”
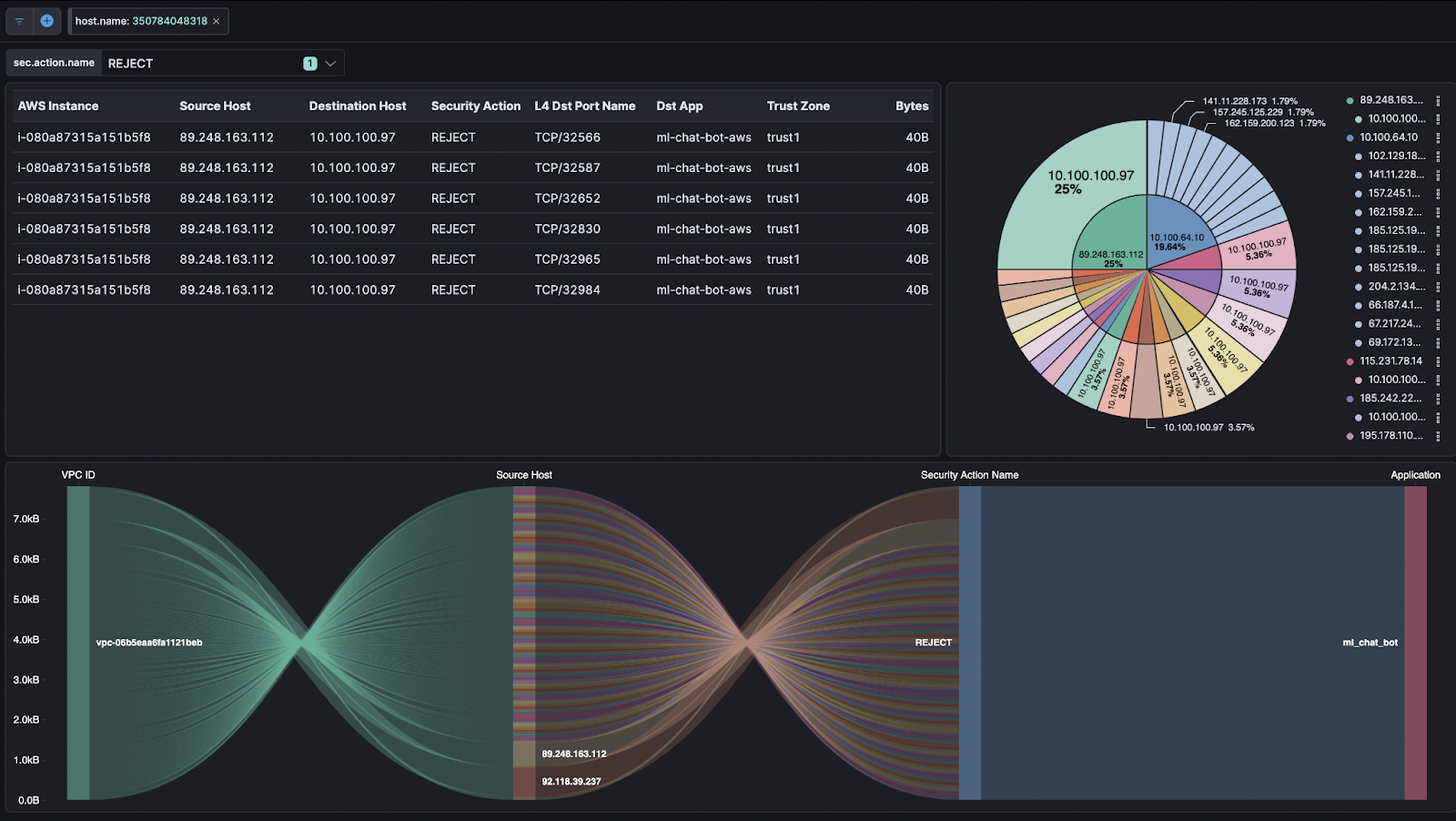
Action: Cross-reference the current firewall to allow rules with flow records to determine which are actively used. If an allowed port hasn’t been observed in flow logs for 60+ days, flag it as a candidate for removal or quarantine testing.
Tip: Look for zero-hit rules—allowed flows with no matching telemetry—especially in high-risk segments like DMZ or inter-zone links.
3. Detect Shadow IT and Unauthorized Access
Use Case: You see generic "ANY ANY" rules to ease cloud migration, but want tighter control.
Action: Review recent flow data to identify unknown client IPs accessing sensitive services. Correlate with asset inventory and identity systems to find unmanaged systems or misconfigured access policies.
Tip: Set up flow-based alerts for unexpected port use (e.g., SSH on non-admin subnets, outbound RDP).
4. Ensure Cloud Workloads Aren’t Bypassing the Firewall
Use Case: After migrating a legacy app to AWS, you may wonder whether it still traverses the on-prem firewall.
Action: Monitor flow logs to confirm the path taken by traffic. Apps often bypass traditional perimeter controls due to peering or direct Internet egress.
Tip: To close visibility gaps, compare cloud-native flow logs (e.g., AWS VPC Flow Logs) flow data with on-prem NetFlow data.

5. Right-Size Access Windows Based on Time-of-Day Analysis
Use Case: You need to allow contractor VPN access, but only during working hours.
Action: Use flow data to determine actual usage windows. Apply time-based firewall rules (if supported) to restrict access accordingly.
Tip: Look for anomalies in off-hours access using time-series flow dashboards.
Enriching Flow Data with ElastiFlow Metadata
Making IPs & Ports Human-Readable
Raw flow data gives you technical details: IP addresses, port numbers, and protocol types. But without context, it’s hard to tell what a flow represents. This is where ElastiFlow metadata enrichment becomes essential.
ElastiFlow automatically enriches flow records with application context by:
Mapping known service ports (e.g., 443 → HTTPS, 3306 → MySQL)
Resolving internal IPs to hostnames, device roles, and functions
Applying custom Application Definitions to associate IP:port patterns with named services
Leveraging SNMP and other inventory data to correlate devices with business functions
Example: From Raw Flow to Application Awareness
Without ElastiFlow enrichment:
src_ip=10.10.2.5 dst_ip=10.10.8.12 src_port=48210 dst_port=8443 protocol=TCP
With ElastiFlow enrichment:
src_app="InventoryService" dst_app="WebOrderPortal"
src_device="app-server-01.acme.local" dst_device="portal-web-03.acme.local"
dst_service="Web HTTPS (8443)"
This enriched view allows analysts to:
Write more precise firewall rules using application identities
Identify legacy services running on non-standard ports
Create application communication matrices for audits or segmentation plans
Use in Cloud and Hybrid Environments
ElastiFlow also supports cloud metadata tagging, such as:
AWS ENI, security group names, block or allow actions
Azure NSG, security rule name, acl id, Azure flow state
Kubernetes namespace and pod labels
This ensures that your flows, whether they originate from a data center, VPC, or containerized workload, are uniformly enriched for maximum clarity.
Tooling Tips
Enable full NetFlow/IPFIX where possible. At a minimum, capture src/dst IP, src/dst port, protocol, bytes, packets,tcp flags,interface ids and timestamps.
Use ElastiFlow’s metadata enrichment to tag flows with meaningful business and technical labels.
Integrate with your firewall manager to enrich flow data with policy rule names, allowing better correlation.
Flow data isn’t just a troubleshooting tool—it’s a strategic asset for firewall lifecycle management. Enriching flow data with ElastiFlow metadata elevates it from raw telemetry to actionable intelligence. Whether you’re migrating workloads, hardening your perimeter, or trimming back legacy access, enriched flow telemetry provides the visibility and evidence you need to act with confidence.
In the hybrid cloud era and distributed workforces, security teams that tap into flow data and metadata enrichment can evolve from rule writers to proactive network guardians.
Stay connected
Sign up to stay connected and receive the latest content and updates from us!