
TCP (Transmission Control Protocol) is a connection-oriented protocol that is foundational to modern network and internet communications. It ensures reliable and ordered data transmission between devices in a computer network.
TCP flags are specific bits in the TCP header used to manage the state and control the flow of a TCP connection. They help devices establish, maintain, and gracefully terminate connections, as well as handle error conditions and manage the flow of data.
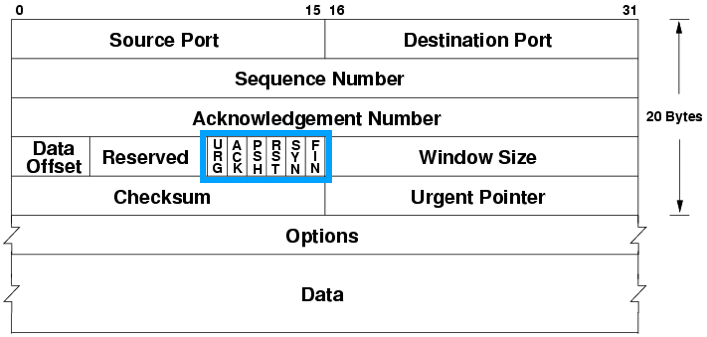
These are the primary TCP flags and their functions:
SYN (Synchronize): The SYN flag initiates a new TCP connection. When a device wants to establish a connection, it sends a TCP packet with the SYN flag set. This process is called the TCP three-way handshake. The SYN flag also carries the initial sequence number for the data stream.
ACK (Acknowledge): The ACK flag is used to acknowledge the receipt of data or to confirm the establishment of a connection. When a device receives a packet with the SYN flag set, it responds with a packet with both SYN and ACK flags. This packet acknowledges the initial request and includes the responder's sequence number. ACK packets are also used to acknowledge the receipt of data during an established connection.
FIN (Finish): The FIN flag indicates that a device has finished sending data and wants to gracefully close the connection. When a device sends a packet with the FIN flag set, it signals that it has no more data to transmit. The other device acknowledges the receipt of the FIN packet with an ACK packet, and then it can also send a FIN packet to close the connection from its end.
RST (Reset): The RST flag abruptly terminates a TCP connection when an error occurs or when a device receives an unexpected packet. When a device receives a packet with the RST flag set, it terminates the connection without waiting for further data or acknowledgments.
PSH (Push): The PSH flag indicates that the packet's data should be immediately delivered to the application layer, bypassing any buffers. This flag ensures that urgent data is processed quickly, even if more data is in transit.
URG (Urgent): The URG flag signals that urgent data is included in the packet. When a device receives a packet with the URG flag set, it processes the urgent data before processing any other data in the packet. The location of the urgent data is specified by the "urgent pointer" field in the TCP header.
While TCP flags are essential in ensuring reliable and orderly communication between devices in a network, cyber attackers may exploit TCP flags to conduct network attacks. They can manipulate or misuse these flags to probe, disrupt, or gain unauthorized access to systems.
Malicious actors know how to manipulate the TCP flags in the handcrafted packets they send. They leverage poorly written firewall rules or access control lists (ACLs) to bypass defenses. This tactic can also "tease" information from hosts protected behind the firewall. By leveraging Network Observability from ElastiFlow, a defender can look for the telltale signs of TCP flag attacks.
Some common network cyberattack vectors that leverage TCP flags include:
SYN Flood Attack: The attacker sends multiple SYN (synchronize) packets with TCP flags set to initiate a connection to the target system. These packets are sent at a high rate, overwhelming the target's resources and causing a denial of service (DoS).
ACK Flood Attack: Attackers flood the target with ACK (acknowledge) packets, even when no prior SYN-ACK exchange has occurred. This can consume network resources and lead to a DoS condition.
TCP Reset (RST) Attack: The attacker sends TCP RST (reset) packets to disrupt an established connection between two devices. An attacker can force the devices to terminate their connection by forging the source and destination addresses.
TCP FIN Scan: Attackers send TCP packets with the FIN (finish) flag set to closed or filtered ports, hoping to receive an RST packet from the target. If no response is received, the attacker can deduce that the port is open, potentially identifying services to exploit.
TCP NULL Scan: Attackers send TCP packets with no flags set, which is an invalid state. Open ports typically do not respond, while closed ports send an RST packet, allowing the attacker to gather information about the target's open ports.
TCP Xmas Scan: This attack sends TCP packets with multiple flags set (such as FIN, URG, and PSH). Like NULL scans, open ports typically do not respond, while closed ports reply with an RST packet. This method helps attackers identify potential targets for further exploitation.
TCP SYN-ACK Reflection Attack: The attacker sends SYN packets with a spoofed source IP address (the victim's IP address) to various systems, sending SYN-ACK packets to the victim. This causes a flood of traffic, leading to a DoS condition for the victim.
These are just a few examples of network cyberattacks that leverage TCP flags. Defending against these attacks often involves proper firewall configurations, intrusion detection systems, and monitoring network traffic for anomalies.
How to Analyze Traffic Patterns and Analyze Abomalites in the Use of TCP Flags
Network flow records, which include information about network traffic such as source and destination IP addresses, port numbers, packet counts, byte counts, and TCP flags, can be used to detect cyberattacks related to TCP flags. By analyzing traffic patterns and identifying anomalies in the use of TCP flags, security analysts can detect potential threats and take appropriate action.
ElastiFlow is a network flow data collection and analytics solution that provides comprehensive analysis and visualization of network flow data, including records from NetFlow, IPFIX, sFlow, and cloud flow logs. ElastiFlow's capabilities can analyze these records, helping to detect cyberattacks related to TCP flags.
Here's how ElastiFlow can be used to detect cyberattacks related to TCP flags using flow records:
Traffic Baseline: ElastiFlow allows security analysts to establish a baseline of normal network traffic patterns, including the distribution of TCP flags. Deviations from the baseline can be flagged for further investigation, helping to detect anomalies and potential threats.

Unusual TCP Flag Combinations: ElastiFlow can analyze NetFlow records for unusual or invalid combinations of TCP flags, helping to detect attacks like NULL scans, Xmas scans, and others that leverage non-standard flag settings to gather information or exploit vulnerabilities.

High Volume of SYN Packets: ElastiFlow can monitor the SYN to SYN-ACK packets ratio, providing insights into potential SYN flood attacks. A sudden surge in SYN packets may indicate an attacker trying to overwhelm the target's resources.

High Volume of ACK or RST Packets: ElastiFlow can help detect ACK flood or TCP Reset attacks by identifying ACK or RST packet count spikes. High volumes of these packets without corresponding SYN-ACK exchanges might indicate such attacks.
Traffic from Unusual Sources: ElastiFlow can help detect potential SYN-ACK reflection attacks by identifying traffic flows where the source and destination IPs are the same or where the source IP address is known to be a spoofed address.
Detection of Port Scanning: ElastiFlow can help identify port scanning attempts by analyzing the sequence of TCP flags in NetFlow records. Port scanning is when attackers systematically probe for open ports on a target system.

Detecting Cyberattacks Related to TCP Flags
ElastiFlow is an effective solution for processing and analyzing network flow records, helping security analysts detect cyberattacks related to TCP flags. Its capabilities for analyzing large volumes of network flow data, generating alerts for potential threats, and providing visualization and reporting tools make it invaluable for network security professionals.
If you found this article helpful and want to try ElastiFlow in your environment, we offer a 30-day trial that is easy to get started with.
Update: ElastiFlow launched NetIntel in June 2024, significantly enhancing threat intelligence with enrichment from our global sensors.
Stay connected
Sign up to stay connected and receive the latest content and updates from us!